
In this blogpost I will concentrate on how we are using Symantec ITMS 8.x to upgrade to the latest Windows 10 Feature Update using a Managed Software Delivery Policy. There are multiple methodes to run an Inplace Upgrade (IPU), for example you could also leverage Patch Management Solution to run the IPU, but in most cases we decided to use a Managed Software Delivery Policy (MSDP) :).
Planning… Planning… Planning
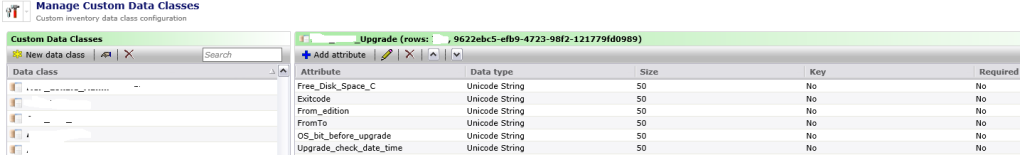
In our case we have already installed the Symantec Management Agent (SMA) with all the necessary Plugins (Software Management Solution Agent and Inventory Agent). When we start to plan the IPU we first generate reports from the clients that will be affected using the already existing Inventory Data. For data that is not captured by default (with Inventory Plugin) but needed we decided to create a Custom Inventory Dataclass and a Task to capture the missing Data.
The Inventory Reports consist of the following data for each computer:
- Hostname
- Hardware Vendor and Model
- Windows 10 Edition (Windows 10 Pro for Workstations, Windows 10 Professional, Windows 10 Enterprise….)
- Windows 10 Feature Version (1507, 1511, 1607, 1703, 1709, 1803, 1809)
- Free Diskspace on C:\
- Anti Virus Vendor (SEP, TrendMicro, Webroot, SEP Cloud, Mcafee….)
- Anti Virus Version
- Harddisk encryption tool (Bitlocker, Symantec Endpoint Encryption….)
- OS Primary Language
- Last Agent Communication
Next we used Microsoft’s Website „Ready for Windows“ to check against the compatibility of AV Versions related to the Windows Feature Version (1909) were we want to upgrade to. Sadly Microsoft decided to discontinue the Website „Ready for Windows“ shortly after creating our report :(. The replacement of the Website „Ready for Windows“ is Microsoft Desktop Analytics.
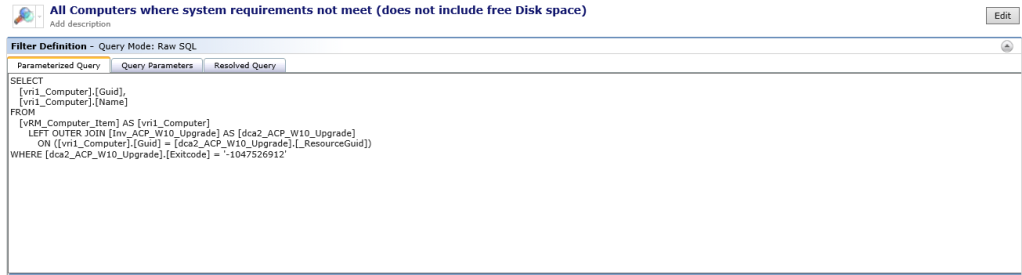
We filtered out computers that did not meet the Hardware Requirements (i.e. Disk Space below 25GB or „Last Agent Communication“ older than 60 days or Computers using a 3rd Party Disk Encryption Tool). Take a look at the reference links at the end of the article for information about Windows 10 Feature Update when using Symantec Endpoint Encrpytion or Symantec Encryption Desktop.
Every System that meets the criteria above is a candidate for the IPU!
On the SMP Server we created a Managed Software Delivery Policy to run the Windows 10 Pre-Upgrade validation using setup.exe (from the original Windows 10 1909 ISO) with the parameter: /Compat ScanOnly.
This will give us additional information if an upgrade will be possible using Microsoft’s own checks (see table below…)
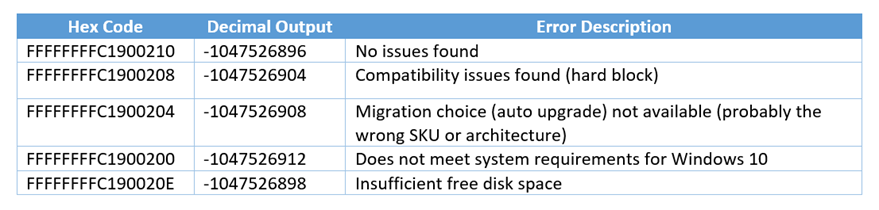
We ran a Powershell script to start „setup.exe“ with the Parameter: /Compat ScanOnly and then we captured the Exitcode („Decimal Output“) and some other information that we also added to the registry. This information will be sent to the previous defined custom dataclass.
"C:\Windows\W10_1909_Upgrade\setup.exe" -Argumentlist "/Auto Upgrade /Quiet /NoReboot /DynamicUpdate Disable /Compat ScanOnly /Priority Normal /CopyLogs C:\windows\temp\W10\W10_1909_Upgrade /BitLocker AlwaysSuspend" -NoNewWindow -wait -PassThru
Attention: For the Pre-Upgrade validation check there is no need to tranfer the whole 4GB down to each client, instead you are able to run setup.exe from a network share – this will prevent unnecessary network traffic. Only computers where the Pre-Upgrade validation check is successful will download the 4GB Windows 10 ISO content.
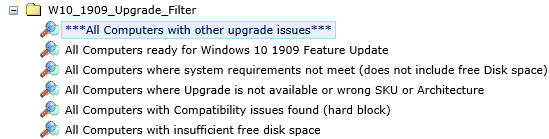
Next we created 6 filters based on the information in the Custom Dataclass which also represent the „Error Description“ found in the table above.
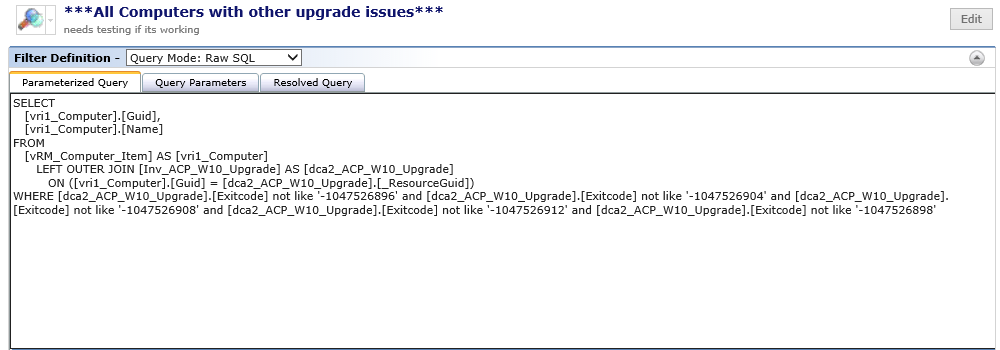
SELECT
[vri1_Computer].[Guid],
[vri1_Computer].[Name]
FROM
[vRM_Computer_Item] AS [vri1_Computer]
LEFT OUTER JOIN [Inv_ACP_W10_Upgrade] AS [dca2_ACP_W10_Upgrade]
ON ([vri1_Computer].[Guid] = [dca2_ACP_W10_Upgrade].[_ResourceGuid])
WHERE [dca2_ACP_W10_Upgrade].[Exitcode] not like '-1047526896' and [dca2_ACP_W10_Upgrade].[Exitcode] not like '-1047526904' and [dca2_ACP_W10_Upgrade].[Exitcode] not like '-1047526908' and [dca2_ACP_W10_Upgrade].[Exitcode] not like '-1047526912' and [dca2_ACP_W10_Upgrade].[Exitcode] not like '-1047526898'
SELECT
[vri1_Computer].[Guid],
[vri1_Computer].[Name]
FROM
[vRM_Computer_Item] AS [vri1_Computer]
LEFT OUTER JOIN [Inv_ACP_W10_Upgrade] AS [dca2_ACP_W10_Upgrade]
ON ([vri1_Computer].[Guid] = [dca2_ACP_W10_Upgrade].[_ResourceGuid])
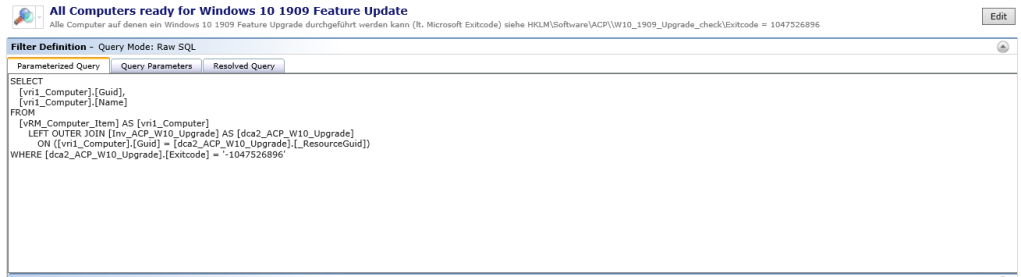
WHERE [dca2_ACP_W10_Upgrade].[Exitcode] = '-1047526896'
SELECT
[vri1_Computer].[Guid],
[vri1_Computer].[Name]
FROM
[vRM_Computer_Item] AS [vri1_Computer]
LEFT OUTER JOIN [Inv_ACP_W10_Upgrade] AS [dca2_ACP_W10_Upgrade]
ON ([vri1_Computer].[Guid] = [dca2_ACP_W10_Upgrade].[_ResourceGuid])
WHERE [dca2_ACP_W10_Upgrade].[Exitcode] = '-1047526912'
SELECT
[vri1_Computer].[Guid],
[vri1_Computer].[Name]
FROM
[vRM_Computer_Item] AS [vri1_Computer]
LEFT OUTER JOIN [Inv_ACP_W10_Upgrade] AS [dca2_ACP_W10_Upgrade]
ON ([vri1_Computer].[Guid] = [dca2_ACP_W10_Upgrade].[_ResourceGuid])
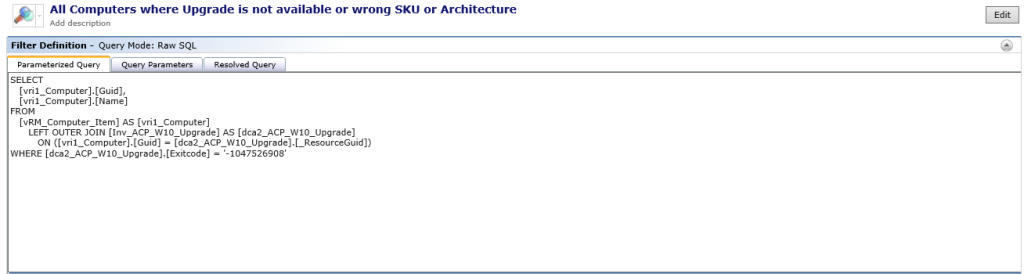
WHERE [dca2_ACP_W10_Upgrade].[Exitcode] = '-1047526908'
SELECT
[vri1_Computer].[Guid],
[vri1_Computer].[Name]
FROM
[vRM_Computer_Item] AS [vri1_Computer]
LEFT OUTER JOIN [Inv_ACP_W10_Upgrade] AS [dca2_ACP_W10_Upgrade]
ON ([vri1_Computer].[Guid] = [dca2_ACP_W10_Upgrade].[_ResourceGuid])
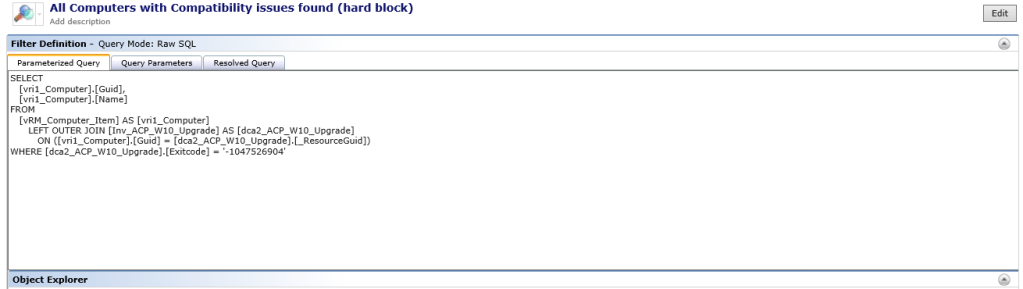
WHERE [dca2_ACP_W10_Upgrade].[Exitcode] = '-1047526904'
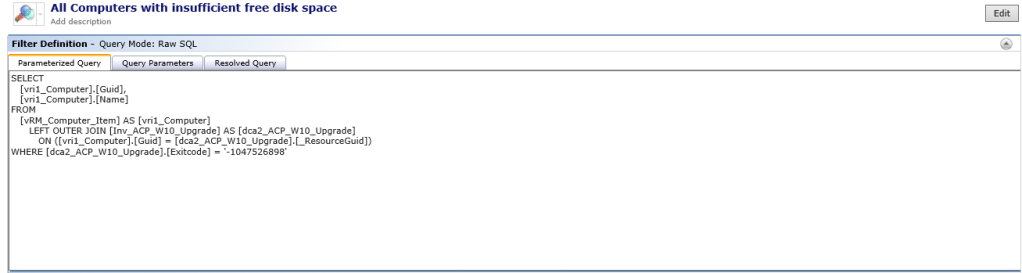
SELECT
[vri1_Computer].[Guid],
[vri1_Computer].[Name]
FROM
[vRM_Computer_Item] AS [vri1_Computer]
LEFT OUTER JOIN [Inv_ACP_W10_Upgrade] AS [dca2_ACP_W10_Upgrade]
ON ([vri1_Computer].[Guid] = [dca2_ACP_W10_Upgrade].[_ResourceGuid])
WHERE [dca2_ACP_W10_Upgrade].[Exitcode] = '-1047526898'
Running the Inplace Upgrade (IPU)
During our tests we found that running setup.exe /Showoobe none Parameter does not work for Privacy Settings, Location Services, Speech recognition, Diagnostics, Relevant Ads… (if there is no GPO that prevents the questions after the IPU…). So we decided to add a few registry keys to prevent the users from answering those questions after the IPU. This also includes settings to prevent the Edge Browser to show the „FirstRunPage“ and so on….
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\MicrosoftEdge\Main] "PreventFirstRunPage"=dword:00000001 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\OOBE] "DisablePrivacyExperience"=dword:00000001 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\InputPersonalization] "AllowInputPersonalization"=dword:00000000 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\CapabilityAccessManager\ConsentStore\location] "Value"="Deny" [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Settings\FindMyDevice] "LocationSyncEnabled"=dword:00000000 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\FindMyDevice] "AllowFindMyDevice"=dword:00000000 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\DataCollection] "DisableDeviceDelete"=dword:00000001 "AllowTelemetry"=dword:00000001 [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\TextInput] "AllowLinguisticDataCollection"=dword:00000000 [HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Privacy] "TailoredExperiencesWithDiagnosticDataEnabled"=dword:00000000 [HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\AdvertisingInfo] "DisabledByGroupPolicy"=dword:00000001 HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CloudContent] "DisableSoftLanding"=dword:00000001
All Computers reporting „Exitcode“ -1047526896 are part of the Filter „All Computers ready for Windows 10 1909 Feature Upgrade“.
We use a MSDP to run the IPU and created a target from the filter „All Computers ready for Windows 10 1909 Feature Upgrade“ in the „Applied to“ section.
To start the IPU we used a Powershell Script… here is the command-line:
"C:\Windows\W10_1909_Upgrade\setup.exe" -Argumentlist "/Auto Upgrade /Quiet /NoReboot /showoobe none /DynamicUpdate Disable /Compat IgnoreWarning /Priority Normal /CopyLogs C:\windows\temp\W10\W10_1909_Upgrade /BitLocker AlwaysSuspend" -NoNewWindow -wait -PassThru
We suspended Bitlocker even though Microsoft says this isn´t necessary anymore…
Our Windows 10 upgrade consists of 3 Major steps – defined by ourself…
- 1st Step starts when the OS is running
- 2nd Step starts after a reboot of the computer (yes, there are multiple reboots…)
- 3rd Step takes place after the IPU during logon of the user
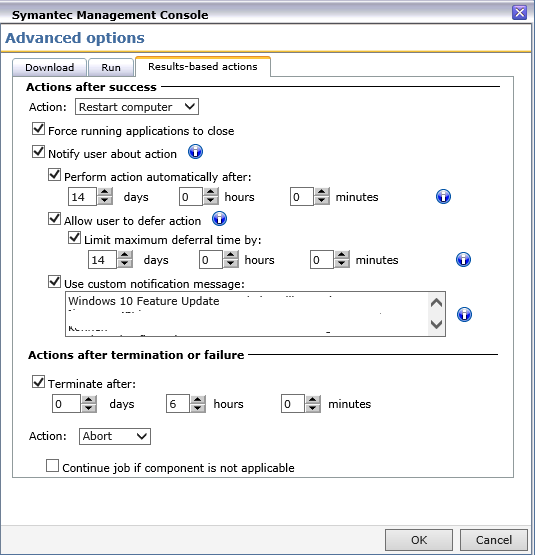
We decided to use the result-based action „restart computer“ available in the advanced options in the MSDP and notify the users about the action and let them defer the IPU for up to 14 days (see screenshot). Another option would be to use the End-User Notification Task with 8.5 RU2. There are other very cool options available to let the users know about the upgrade – one of my favorite is the Windows 10 Toast Notification Script from Martin Bengtsson.
After running the IPU we created another custom inventory to check on the status and to capture additional information about the upgrade.
In addition we are also storing the Information captured for the custom inventory data in each computers registry.
That´s it!
reference links:
- Windows Setup Command-Line Options
- Deploying Win10 Feature Updates Via Software Portal
- Upgrading to Windows 10 or upgrading an existing version of Windows 10 using Software Management Solution
- Windows 10 Pre-Upgrade Validation using SETUP.EXE
- Get help with Windows 10 upgrade and installation errors
- Windows 10 Toast Notification Script
- How to upgrade computers encrypted with Symantec Encryption Desktop to a Windows 10 release
- How to upgrade computers encrypted with Symantec Endpoint Encryption to a Windows 10 release
- Using Patch Management Solution to deploy Windows 10 feature updates to endpoints with drive encryption